Managing large numbers or servers can be quite cumbersome, especially when your logs are not centralized. In the past I have managed clusters of servers. One such cluster was acting as a mail filter for a large number of customer mailboxes. Without centralized logging acting on a customer support ticket would involve logging into every server to read the logs.
We can avoid this cumbersome process by using centralized logging, in this case our log server will be a Synology DiskStation running DSM 5.1. Once configured, the logs from our servers will be sent to the Synology DiskStation making it really easy to search for log events across multiple servers from one interface.
First thing first we need to tell the Synology DiskStation where it should be saving our log files. We can do this by opening Log Center and clicking on Storage Settings. You will see an option called Destination use this to configure a folder location to save the log files. In our case the log files are being saved to /volume1/storage/logs. There are some other options available to do with archiving but we will not be going into these and just use the defaults, you are welcome to experiment with your own settings. Once you are happy with the setting click on the Apply button.
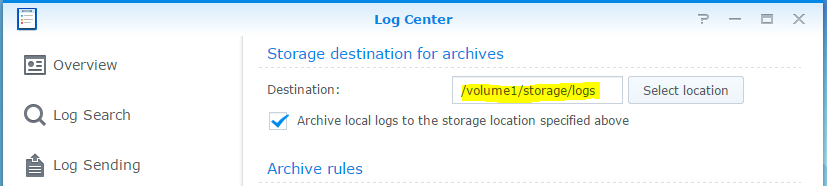
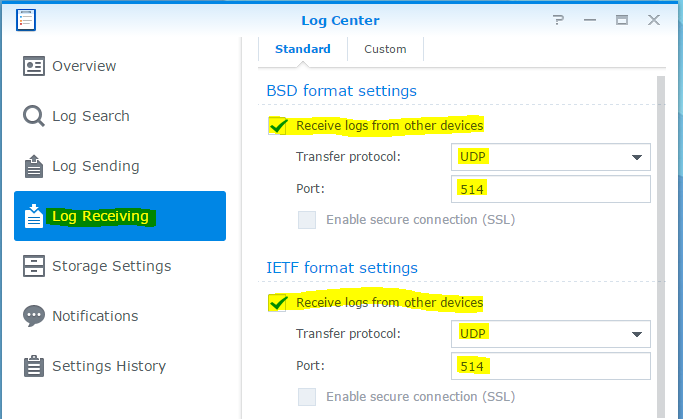
The next step is to actually enable Log Receiving within the Log Center, it’s pretty easy. Click on Log Receiving on the left hand side. In our case we have enabled the Log Center to receive logs in BSD and IETF formats. Again click on the Apply button, in the next step we will start chucking some logs at the Log Center.
Now we need to start sending some logs to the Log Center. We are going to do this with a CentOS 7 virtual machine by making some changes to rsyslog. The great thing about rsyslog is that we can continue to have local log files and also send them to a syslog server at the same time.
You will need to use your favorite editor to edit the log file. My favorite is nano it’s considerably easier to get used to than vi.
nano /etc/rsyslog.conf
At the bottom of the rsyslog.conf file add the following, replace <IPADDRESS> with the IP Address of your DiskStation.
*.* @<IPADDRESS>:514
In our case the IP Address of the DiskStation is 10.0.0.1, so our line in rsyslog.conf will look like the following.
*.* @10.0.0.1:514
Make sure to save your changes and quit out of the editor, in nano we can do this by pressing Ctrl+x nano will then prompt us to save the file. Just save the file with the same file name.
Finally you should restart rsyslog, to do this on CentOS 7 you should use the following command.
systemctl restart rsyslog
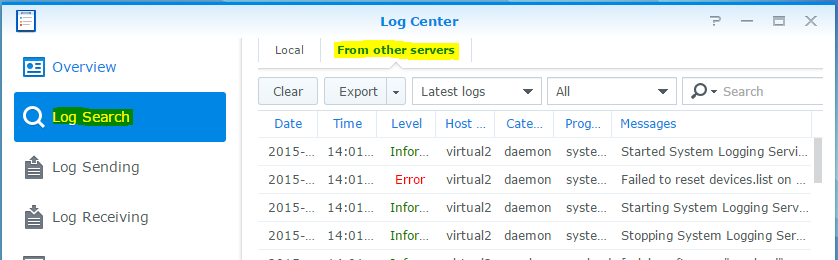
You can now search for logs in the Log Center by going to Log Search and then click on From other servers it should look something like the following.